Cybersecurity
i-PRO Cybersecurity Policy
Cyber-attacks are rising every day, and Industrial Internet of Things (IIoT) devices such as cameras are prime targets for attackers. We understand that resilient surveillance systems are an important part of any security system, and with that in mind, we work hard to make sure that we do our best to keep IIoT devices secure.
i-PRO products are designed, developed and verified to be secure by using industry standard security frameworks and development best practices, helping to protect users from possible cyberattacks.
PSIRT
i-PRO’s Product Security Incident Response Team (PSIRT) is dedicated to designing proactive safeguards against unauthorized device access and intrusions, as well as, addressing security vulnerabilities as they are disclosed.
- The PSIRT Motto
“Customer safety and security is paramount. We are proactively improving product security and are quick to address critical vulnerabilities.”
- Updated Software and Firmware Release Process
Continuous upgrades to our products, systems and services are implemented throughout our products’ life cycles and released as needed through our product webpage.

Education
Hardening Guide
i-PRO wants to make it as easy as possible to secure our devices. For your convenience we have created several product hardening guides that are available through our website. Hardening guides include best practices to secure our hardware and software, along with instructions on how to do so.
White paper
i-PRO Built-In Cybersecurity Features:

Authentication
The basic method of preventing unauthorized access to surveillance equipment is to set a username and password to restrict access. i-PRO cameras support further authentication functions, such as digest authentication, host authentication and IEEE 802.1X.

Secure Communication
i-PRO cameras support mutual authentication for secure communication, such as SSL and TLS.
SSL/TLS communications use pre-installed certificates on i-PRO cameras to provide an encrypted communication to help prevent eavesdropping and spoofing of devices.

Data Encryption
Data encryption secures the video and audio data so that is it unusable to anyone that intercepts the traffic. i-PRO cameras do this through secure protocols such as HTTPS and RTSP. Any audio or video stored on the SD card can also be encrypted in case the device is compromised.

Alteration Detection
The Alteration Detection feature checks if video or audio (MP4) files have been modified. i-PRO cameras support Alteration Detection on the camera SD card by using certificates pre-installed in i-PRO cameras and the Integrity Verifier tool.
*Some of these features are only available on our S series cameras.
White paper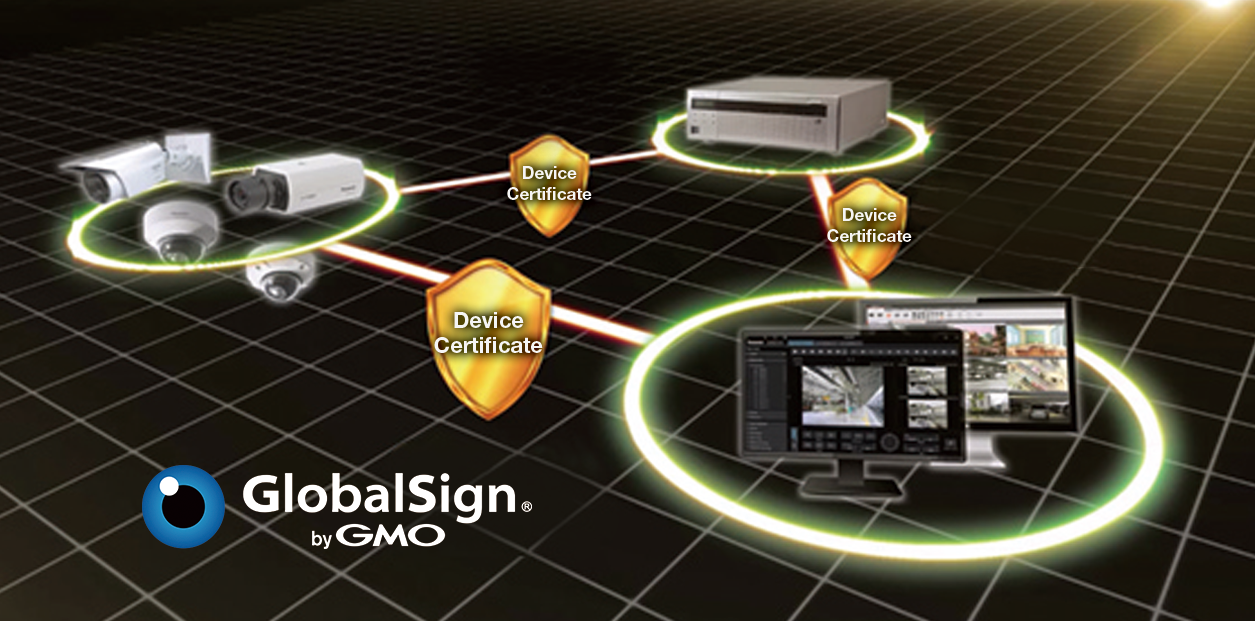
GlobalSign Certificates Come Pre-Installed
i-PRO uses trusted third-party certificates from GlobalSign and our own in-house embedded cryptography technology to provide a highly secure and robust protection layer. Third-party certificates ensure that the certificates come from a trusted source.
FIPS 140-2 Level 3 Certified Secure Element* *EdgeLock® SE050F (NXP® Semiconductors)
A Secure Element* is a chip that is built into many of our new S-series cameras and is used to prevent unauthorized access and store confidential and cryptographic data.
Selected i-PRO cameras have an embedded Secure Element* with Trusted Platform Module (TPM) functionality which is certified FIPS 140-2 Level 3 compliant.
- i-PRO camera models complies with FIPS 140-2 level3
Click Here
FIPS 140-2
Federal Information Processing Standards (FIPS) are standards and guidelines for U.S. federal computer systems that are developed by the National Institute of Standards and Technology (NIST). This standard security requirement for encrypted modules is specified in the FIPS 140-2 section.
White paper
End-to-End Security
i-PRO provides end-to-end security solutions for its video surveillance products. Video and audio that are not encrypted can be intercepted by unauthorized parties to be viewed, listened to, or modified without consent. In order to protect against this type of attack, i-PRO offers users the ability to encrypt video and audio while it is being transferred to a network video recorder (NVR) and video management system (VMS) using secure protocols.

SRTP With Genetec Security Center
Secure Real-Time Transfer Protocol (SRTP) is a protocol for encrypting RTP packets and streaming data. In an SRTP communication, the RTSP protocol is encrypted by SSL and used with Genetec Security Center to encrypt data in transit, so there is no risk of unauthorized viewing of usernames or passwords.

i-PRO Configuration Tool (iCT)
iCT is an innovative tool that enables you to operate up to 1,024 cameras or NVRs connected to a centralized video surveillance system as well as conduct day-to-day maintenance.
The following setting changes in the security system can be done comprehensively through iCT preferred CA certificates: HTTPS, TLS/SSL, and IEEE 802.1X.
Learn MoreCompliance
NDAA compliant
i-PRO is proud to confirm that our products are compliant under the National Defense Authorization Act (NDAA). Our company was founded on the principles of trust, safety and security. We are committed to ensuring that our products meet the needs of all our customers and that we continue being a trusted partner to our educational clients and our federal, state and local governments.
