
Over the next few blog posts, I’ll show you some of the common ways that hackers can and will take advantage of your Internet of Things/Industrial Internet of Things (IoT/IIoT (Internet of Things/Industrial Internet of Things) devices. Ii-PRO will be launching a mini-series of sorts called “Hacking IoT” that will focus on some of the ways that hackers discover IoT devices, target them, and exploit them. So, sit down, buckle up, and always keep your arms in and legs inside the ride at all times, because here we go!
*A Quick disclaimer:, It is illegal to hack or compromise someone’s system without express permission from the owner —– DO NOT try this at home!
Sometimes as a cybersecurity professional, I feel like the proverbial Chicken Little always yelling about the sky falling. In this “Hacking IoT” miniseries I want to show you exactly how these attacks are carried out, that way you can make your own judgement as to whether the sky is indeed falling.
One of the first questions that I’m often asked is, “How do hackers even know that my device is there?” This is a great question. Every device that is on the internet needs to be able to communicate to perform its function., These communications are often done through ports, protocols, and services. This information can be used to “fingerprint” or identify the device that is connected to the internet, which can be a homing beacon to hackers.
Let’s explore an example that everyone reading this article can relate to, but might not think about, is. Every time you access a website, you are using ports, protocols, and services. If you go to a secure website, for example, you are using port 443, the HTTPs protocol, and the web service. The web server hosting that website would be advertising those ports (443), protocols (HTTPS), and services (web service) to let your computer know that there is a website here. What does this have to do with discovering IoT devices? Everything! Just like the web servers, IoT devices use ports, protocols, and services that are unique to them, and hackers can use this information to find devices without ever leaving their couches.
Let’s look at it this another way. Let’s say that I asked you to describe a car to me. You might say something like, “it It has at least four wheels, has a steering wheel, an accelerator pedal, and two headlights.” Those are some good characteristics, and if I walked around my neighborhood, I might see other devices that fit that description (like riding lawnmowers for example), but for the most part, I’m going to discover cars. Scanning the internet for devices is basically the same thing., We have a general description of the devices we want to find and use that as our search criteria.
Ok, enough talking, let’s do this. So how do hackers find IoT devices? One of the ways they discover devices is by using scanners, which is what I’ll be demonstrating today. For this demo I’ll be using a tool called SHODAN. SHODAN is a publicly available internet scanning device that crawls through the web 24/7, scanning and saving characteristics of every device on the internet. With a tool like SHODAN you can look at specific IP addresses, port numbers, device information, locations, and a ton of other options. There are 1,000sthousands of ways to scan with SHODAN, but for this example, I’m going to try to find an open camera that is near me (here in Pensacola, FL).
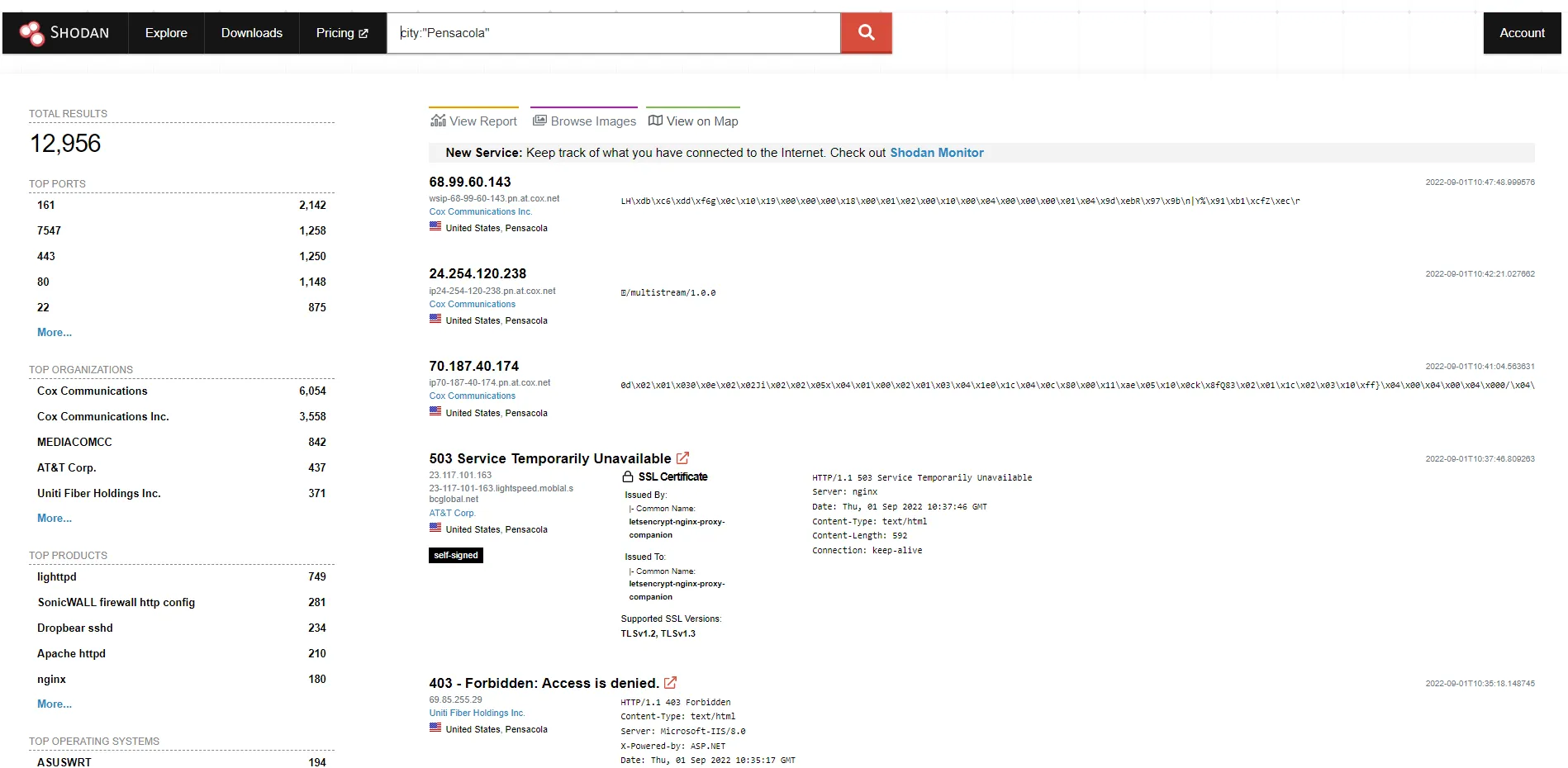
Step 1. I’m going to filter on City, and in my case, I’m going to use my current location of Pensacola, FL. So I’ll search city:”Pensacola”. Here you can see that there are 12,956 devices returned with various ports, organizations, and products.
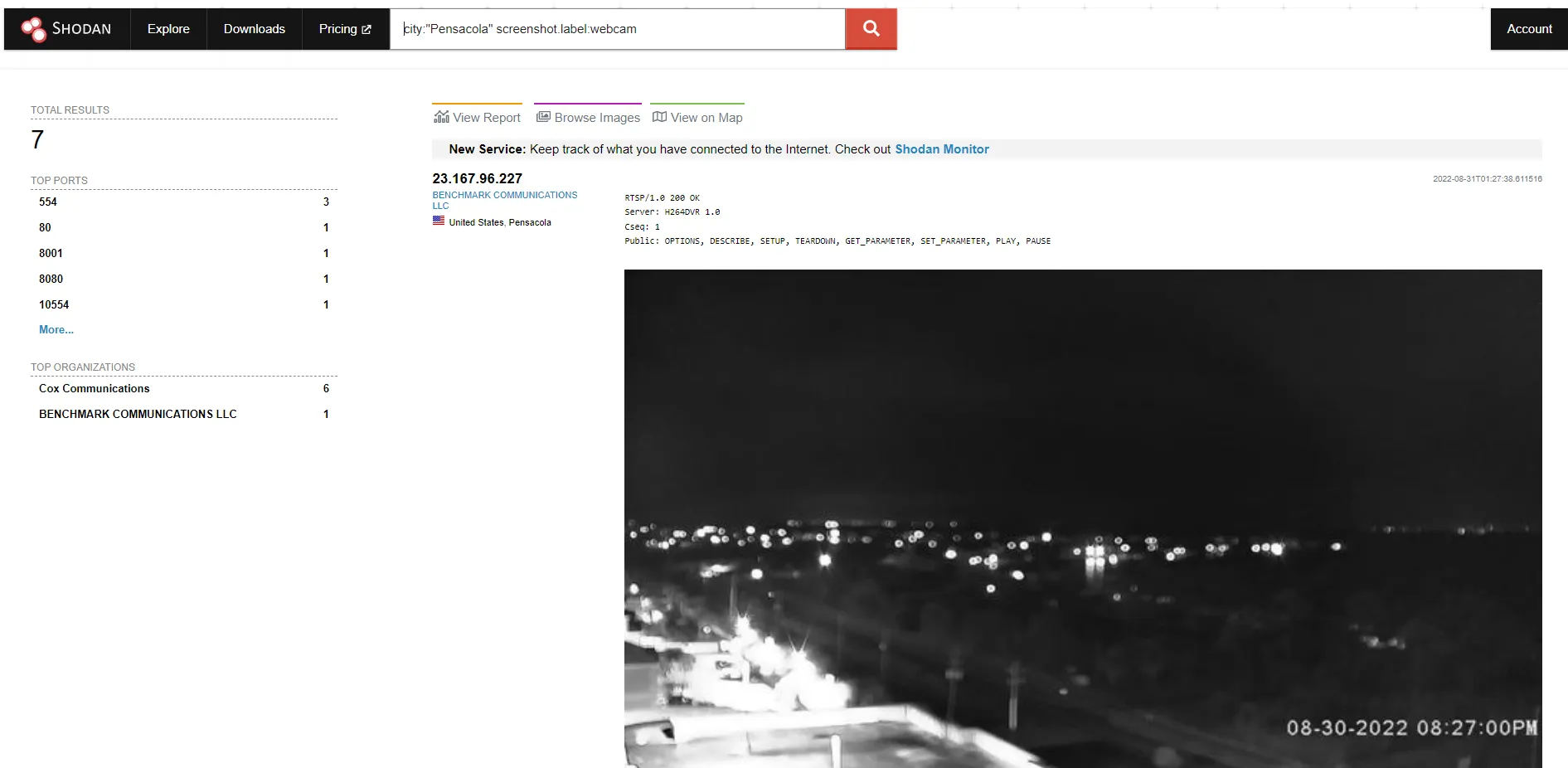
Step 2. Since this is just a demo, I’m now going to use a search that I know will show me good webcam data, so I’ll add “screenshot.label:webcam” to my search so that I can see some webcam feed.
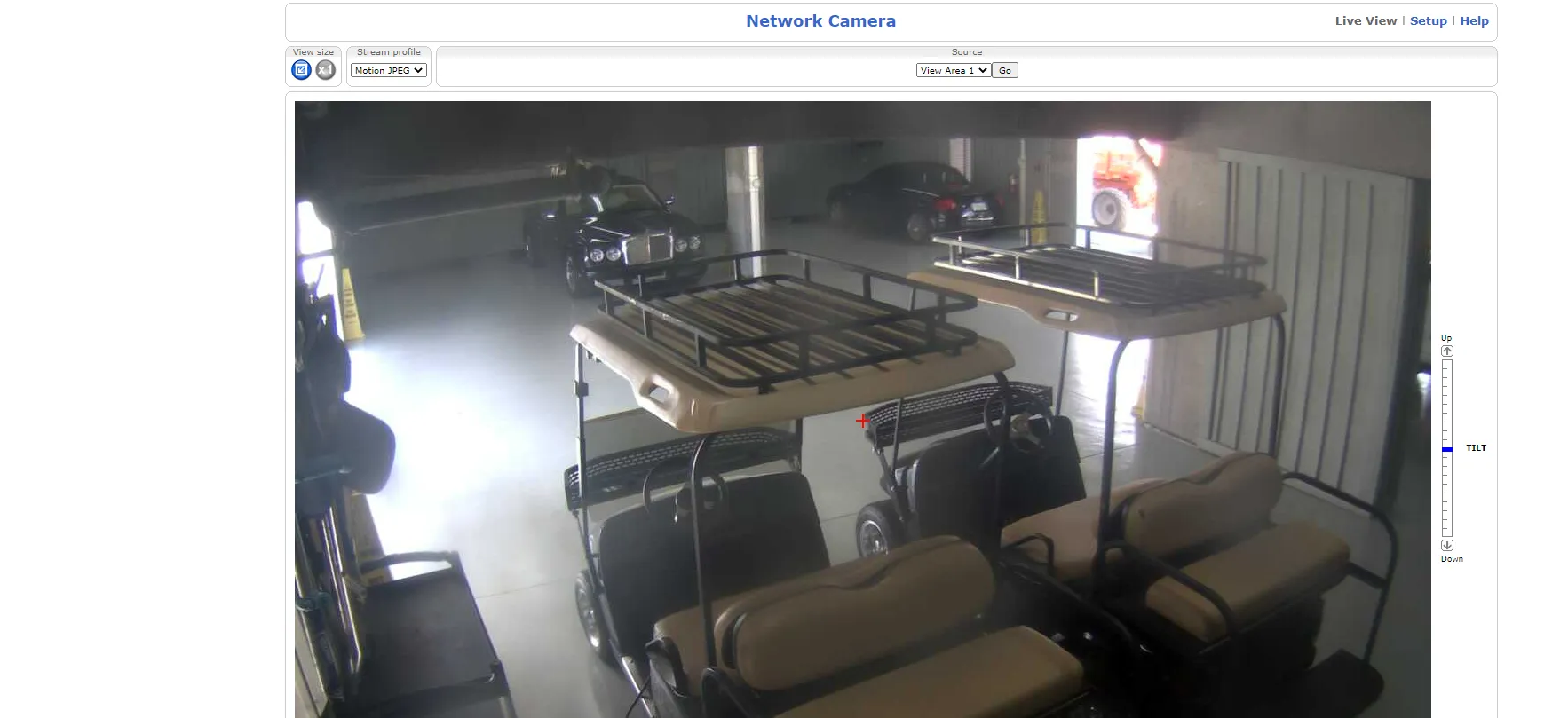
Step 3. I’ll look for a good target by scrolling through the results. This person has a lot of nice cars., I think I’ll check out their camera.
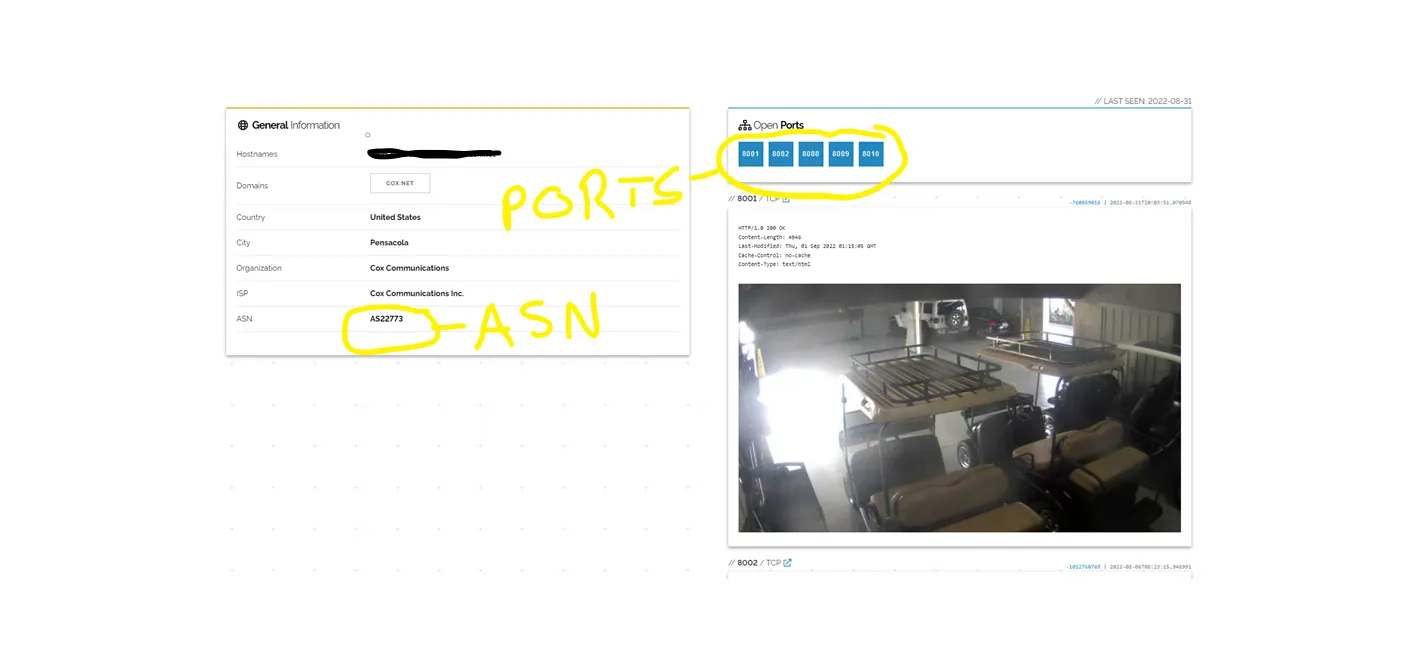
Step 4. I’ll examine the details of this camera to see if I want to use any of these parameters on future searches. For example, if I wanted to find more of this manufacturers cameras, I can look to see what ports this one is using, or I could search using the autonomous system number (ASN) that will be unique to this device.
Step 5. For now, I’m just going to view the live camera feed. From the previous screen shots from the camera feed, I can see that several of the cars are missing. Maybe no one is home? Maybe if I watch long enough, I can see where they keep their keys…
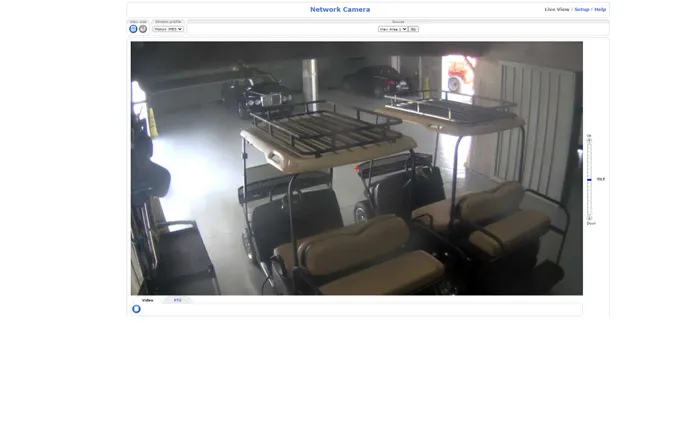
And there you have it! A simple demonstration on how hackers discover IoT devices. There are a lot more searches that are possible on SHODAN, . Just remember that it is illegal to compromise someone else’s system without permission.
How can you defend against this type of attack? Never let IoT/IIoT devices face the internet. Use hardened network settings and segmentation to ensure that these types of devices are not accessible from the outside. And make sure to use strong passwords to protect these devices. For more tips, be sure to check out my previous post on IoT Security and Best Practices.
Come back next month and I’ll show you how to do carry out a custom Social Engineering Attack!